Blind XSS Vulnerability on Googleplex.com Invoice Portal
Google, as a global technology leader, relies on thousands of suppliers worldwide to sustain its vast operations. To efficiently manage and process payments, Google provides an online platform where suppliers can submit their invoices directly. This system, known as the Google Invoice Submission Portal, was designed to streamline supplier invoicing through a web interface accessible at gist-uploadmyinvoice.appspot.com.
Overview of the Google Invoice Submission Portal
The portal allows suppliers to upload invoices related to purchase orders for processing. Notably, the site was hosted on a Google App Engine domain with the appspot.com suffix, a common Google infrastructure for internal and developmental applications. Typically, production systems are migrated to official Google domains such as google.com, but in this case, the portal remained accessible on the public App Engine domain.
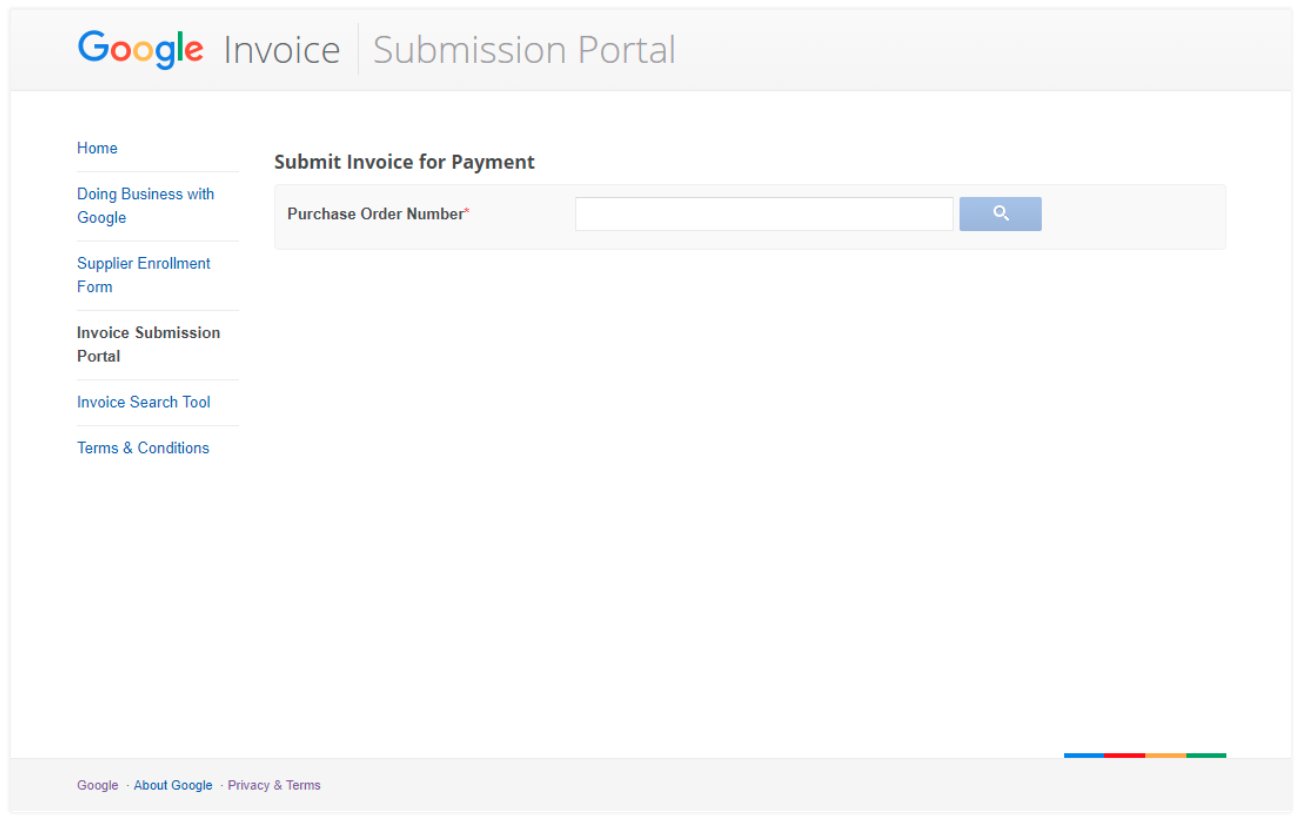
Invoice Upload Process
- Enter Purchase Order Number: Users input a purchase order number to locate related invoices. Oddly, the field accepted any input without validation.
- Select Organization: Suppliers choose an organization linked with the invoice, affecting processing locale and regulatory compliance.
- Submit Invoice Details: The form then prompts for an email address, invoice number, invoice date, and a PDF file upload representing the actual invoice.
Identifying Vulnerabilities: Blind Cross-Site Scripting (XSS)
The author tested the input fields with typical XSS payloads to check for reflected or stored script injection vulnerabilities. No immediate errors or triggers were observed, indicating that text inputs were properly sanitized or escaped.
However, the critical vulnerability resided in the file upload mechanism. Although the form restricted uploads to PDF files via front-end validation, this was insufficient to prevent tampering. By intercepting the file upload request using a web proxy debugger, the attacker was able to modify the filename and content type from .pdf and application/pdf to .html and text/html, respectively, and insert a malicious script payload.
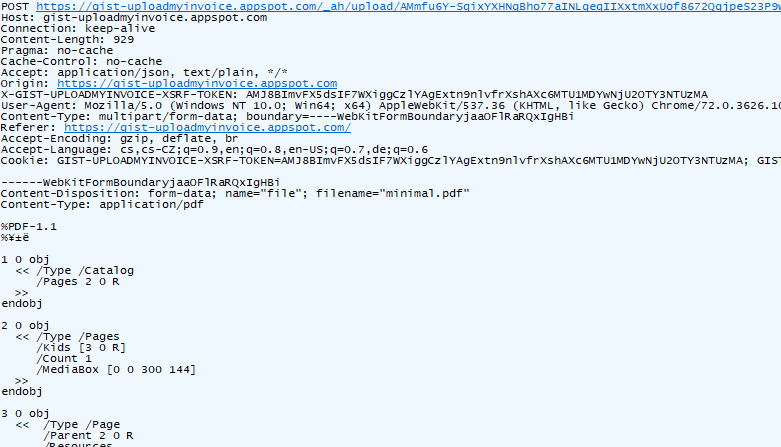
This attack enabled blind XSS, where the malicious script is stored but not immediately executed. Instead, the payload triggered later when a Google employee accessed the invoice within an internal application hosted on the googleplex.com domain. Since googleplex.com hosts internal Google systems, access to that domain is restricted to employees via authentication.
Execution and Impact of Blind XSS
After submitting the tampered HTML file disguised as an invoice, the attacker received notification that the payload was executed on a googleplex.com subdomain. The internal dashboard rendered the uploaded file with a text/html content type, executing the attacker’s JavaScript code.
This scenario illustrates how improper content-type validation and insufficient sandboxing can lead to critical vulnerabilities in internal systems, even within large organizations like Google.
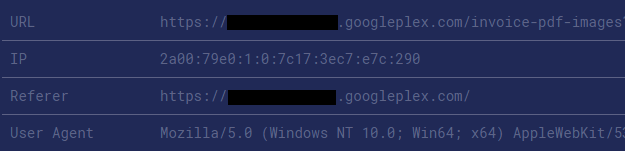
Potential Security Consequences
- Access to Sensitive Data: The script could expose highly confidential information such as internal invoices.
- Session Hijacking Risks: Although initial assumptions suggested that the attacker could impersonate employees across other internal apps, Google’s security team clarified this was not the case due to strict isolation and CORS policies.
- Internal Trust Boundary Breach: Execution within an authenticated employee’s context undermines the trust and security of internal applications.
Google’s Response and Resolution
The issue was promptly reported to Google’s security team, receiving escalating priority due to its severity. Within weeks, Google deployed a fix that mitigated the vulnerability by sandboxing uploaded content. Post-fix, any script execution occurred only on isolated storage domains like storage.googleapis.com, which are sandboxed and do not grant access to internal systems.
Google’s resolution effectively prevented the blind XSS from impacting authenticated internal systems, underscoring the importance of isolating user-generated content and validating file uploads comprehensively.
Key Insights and Lessons Learned
This case underlines important security concepts relevant to web application security:
1. Blind XSS Explained
Blind XSS is a stored cross-site scripting attack where the executed script is triggered in a context inaccessible to the attacker, often an internal dashboard or admin panel. Such vulnerabilities are especially dangerous since they can bypass initial detection.
2. File Upload Validation Is Critical
Client-side enforcement of allowed file types, like restricting to PDF, is easily bypassed. Servers should implement both content-type verification and content inspection to prevent execution of malicious scripts disguised as permitted files.
3. Sandboxing User Content
Storing user-generated content on isolated domains or sandboxed environments minimizes risk if malicious scripts do execute. This technique is recognized as a best practice for containing potential damage.
4. Internal App Security Boundaries
Google’s clarification that subdomains like googleplex.com host independent applications with isolated sessions reflects a robust security design preventing lateral movement within internal services.
Broader Context and Statistics on Blind XSS
- According to the 2023 PortSwigger Web Security Report, XSS vulnerabilities remain among the top ten most common security issues, affecting approximately 11% of tested applications globally.
- Blind XSS attacks have notably increased due to expanded use of third-party integrations and internal dashboards that process untrusted content without stringent sanitization.
- The Open Web Application Security Project (OWASP) emphasizes blind XSS as particularly dangerous in sensitive environments such as enterprise intranets and cloud platforms.
Conclusion
The discovery of a blind XSS vulnerability in Google’s Invoice Submission Portal highlights the persistent risks posed by insufficient input validation and secure content handling. Even industry-leading companies must vigilantly enforce security best practices, such as thorough server-side validation, sandboxing of uploads, and isolating internal applications to reduce impact in case of breaches.
Security researchers, developers, and organizations can draw valuable insights from this case to strengthen their defenses against blind XSS and similar threats.
Summary of Best Practices to Prevent Blind XSS Vulnerabilities
- Implement strict server-side content-type checks and file validation.
- Utilize sandboxed or isolated domains for hosting uploaded content.
- Sanitize and escape all user inputs, especially those displayed in internal dashboards.
- Enforce application-level session and domain isolation to prevent cross-app impersonation.
- Regularly conduct penetration testing focused on blind XSS and other stored XSS variants.



