What Is SSL/TLS? Understanding TLS Security Protocols
Secure Sockets Layer (SSL) and Transport Layer Security (TLS) are foundational cryptographic protocols designed to secure network communications. Their primary objectives are to ensure data integrity and maintain communication privacy across the internet and other networks. While SSL was the original protocol developed for these purposes, it has since been supplanted by TLS, which offers enhanced security and improved performance. Modern web browsers and applications have deprecated SSL entirely due to its vulnerabilities and rely exclusively on TLS.
The Role of SSL and TLS in Network Security
Both SSL and TLS are widely employed to protect the communication channels between clients—such as web browsers or email clients—and servers. TLS serves as the backbone of secure connections for multiple protocols, including HTTPS (HTTP Secure), SMTPS (Secure SMTP), FTPS (FTP Secure), SIP Secure, and VPN tunnels. Typically, the addition of an “S” at the end of a protocol indicates that it uses SSL/TLS to encrypt its data in transit.
The OpenSSL library is among the most common software implementations of SSL/TLS, providing robust and tested cryptographic functions that underpin secure communications in countless applications worldwide.
Core Cryptography Behind SSL/TLS
SSL and TLS function as frameworks that employ various cryptographic algorithms during the connection process. These algorithms include:
- Asymmetric encryption: Algorithms like RSA and Elliptic Curve Cryptography (ECC) for key exchanges and authentication.
- Symmetric encryption: AES and ChaCha20 for encrypting session data.
- Hashing and message authentication: SHA-2 family and HMAC to ensure data integrity.
- Key exchange protocols: Diffie–Hellman (DH), including ephemeral versions (DHE, ECDHE) to facilitate Perfect Forward Secrecy.
During the initial handshake, communicating parties negotiate which cipher suite to use based on supported algorithms and security preferences.
The latest version of TLS, 1.3, standardized in RFC 8446, streamlines the handshake for better security and lower latency, removing obsolete and vulnerable cryptographic mechanisms present in earlier versions. SSL 3.0, which predates TLS, is defined in RFC 6101, but it is now considered insecure and deprecated in all modern implementations.
Privacy and Data Integrity: Why Encryption Matters
One of the vital purposes of SSL/TLS protocols is to encrypt the data transmitted between client and server, preventing unauthorized entities from reading or altering sensitive information.
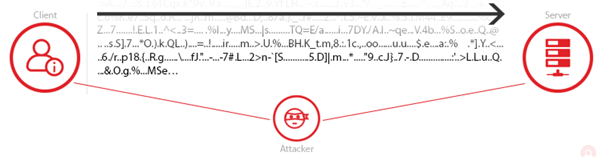
Without encryption, network traffic such as usernames, passwords, financial details, or authentication cookies travel as plain text, easily intercepted via passive sniffing or active man-in-the-middle (MITM) attacks. For example, accessing an administration portal over an unencrypted connection can expose session cookies that attackers can use to hijack accounts.
Conversely, when SSL/TLS encrypts the connection, intercepted data appears as random ciphertext, rendering it useless to attackers without the proper cryptographic keys.

Authentication and Verification Through Certificates
Beyond encryption, SSL/TLS protocols provide authentication mechanisms to verify the identities of communicating parties. This authentication is essential in online transactions, where confirming the true identity of a server—and in some cases, a client—is paramount.
During the handshake, the server presents an SSL/TLS certificate, which acts as a digital passport. Clients verify this certificate against a trusted Certificate Authority (CA) list embedded within their operating system or browser. Certificates are digitally signed by CAs, ensuring they cannot be fabricated or altered without detection.
This process guarantees that users connect to legitimate servers, protecting them from impersonation and phishing threats.
Perfect Forward Secrecy: Enhancing Long-term Security
Perfect Forward Secrecy (PFS) is a critical security feature that ensures session keys used in SSL/TLS connections are ephemeral and cannot be retrospectively decrypted even if the server’s private key is compromised in the future.
PFS achieves this by generating unique keys for each session through ephemeral key exchange algorithms like DHE or ECDHE. Consequently, an attacker gaining access to long-term private keys cannot decrypt past recorded communications, significantly mitigating the risks of data breaches.
Contemporary Importance of TLS in Cybersecurity
Recent studies highlight the continuous growth in web traffic secured by TLS. According to Google Transparency Report, as of early 2024, over 95% of web traffic from Chrome browsers is encrypted using HTTPS, backed by TLS.
This widespread adoption reduces the attack surface for interception and data theft. However, vulnerabilities and attacks targeting flawed TLS implementations persist, underscoring the necessity of keeping TLS versions and cipher suites updated and configuring servers securely.
Emerging protocols such as QUIC, which integrate TLS 1.3 directly for low-latency encrypted communication, indicate blockchain of secure communication technologies in next-generation internet applications.
Summary of Key SSL/TLS Features
- Encryption: Protects data confidentiality by encrypting communications.
- Integrity: Ensures data is not tampered with during transmission.
- Authentication: Verifies the identity of servers and clients through certificates.
- Perfect Forward Secrecy: Guards past communications from future key compromises.
- Interoperability: Supported by almost all major internet protocols and software.
Conclusion
SSL/TLS protocols are indispensable elements of modern internet security, safeguarding data privacy, and establishing trustworthy communication channels. While SSL played a pioneering role historically, TLS has emerged as the secure and efficient successor. Implementing the latest TLS versions with robust cipher suites and ensuring certificate validity are key practices in defending against cyber threats and maintaining user trust.