What is Phishing? Understanding the Growing Cyber Threat
Phishing remains one of the most pervasive and dangerous cyber threats affecting individuals and organizations worldwide. Its continuous evolution and increasing sophistication have made it a top concern in cybersecurity today. From fraudulent emails impersonating banks to malicious links spread through collaboration tools, phishing attacks aim to deceive users into revealing sensitive data that can lead to identity theft, financial loss, or system compromise.
Defining Phishing: The Cybercriminal’s Bait
Phishing is a type of cyber attack in which criminals attempt to fraudulently obtain sensitive information by masquerading as trustworthy entities. This sensitive data, often called personal identification information (PII), includes but is not limited to:
- Usernames and passwords
- Credit card details
- Social Security numbers
- Bank account information
- Email and phone numbers
- Answers to security questions
Even partial data can increase a hacker’s chances of successfully launching subsequent social engineering attacks or breaching accounts.
Phishing attacks often leverage trusted brands such as banks, internet providers, retail stores, or communication platforms to lure victims into engaging with malicious content, typically through emails, messages, or fake websites.
Common Types of Phishing Attacks
Phishing is no longer limited to deceptive emails. Attackers have diversified their tactics to evade detection and exploit new communication channels. The major phishing types include:
1. Deceptive Email Campaigns
This is the classic and most widespread form of phishing. Attackers send emails that appear to come from trusted sources, prompting recipients to click on links or provide confidential information urgently.
Due to advancements in anti-spam technologies, many phishing emails get blocked before reaching inboxes. However, carefully crafted phishing campaigns still manage to bypass filters, especially targeted campaigns.
Example: In 2018, a phishing campaign targeted WordPress site owners with fake database upgrade notices hosted on hacked legitimate sites. Clicking the link opened a counterfeit WordPress login page designed to steal user credentials.
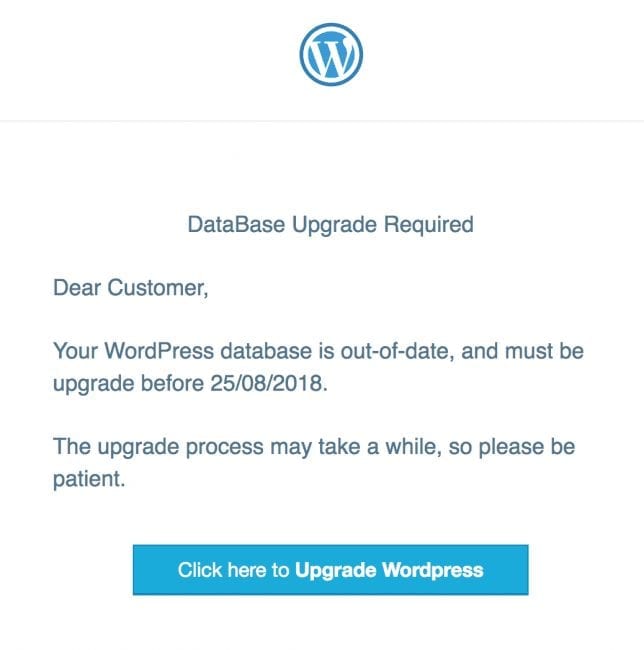
2. Phishing via Collaboration Tools and Cloud Services
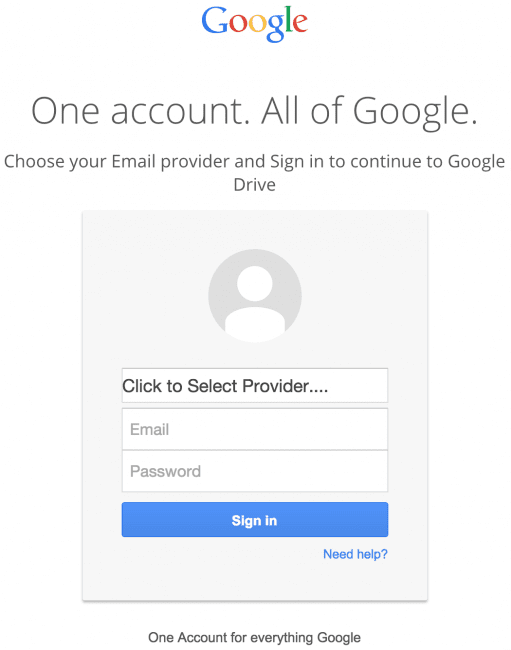
With the rise of remote work, phishing attackers exploit popular cloud platforms like Google Workspace, Microsoft 365, Slack, and Dropbox. They send fraudulent “share” notifications or embed malicious links in documents and calendar invites, tricking users into granting access or entering credentials.
Example: Users receiving a Google Drive phishing link often see pages that mimic legitimate Google login screens but are designed to harvest credentials.
3. Spear Phishing
Unlike broad campaigns, spear phishing targets specific individuals or organizations with personalized and well-researched messages. Attackers may gather information from social media to craft convincing emails, increasing the likelihood of success.
Spear phishing often aims at stealing significant assets, conducting espionage, or compromising internal systems by targeting intermediaries such as assistants or accountants.
Emerging Trend: Artificial Intelligence (AI) now enables attackers to generate tailored, grammatically flawless spear phishing messages and even mimic writing styles, significantly increasing threat sophistication and success rates (source: CSO Online, 2024).
Phishing Statistics Highlighting Its Growing Threat
- The Anti-Phishing Working Group (APWG) reported over 270,000 unique phishing attacks in Q1 2024 alone, representing a 30% increase year over year (APWG, 2024).
- More than 90% of data breaches start with a successful phishing attack (Cybersecurity Ventures, 2024).
- Organizations lose an average of $4.65 million per data breach, often triggered by phishing (IBM Data Breach Report, 2024).
Key Prevention Strategies against Phishing
Successful defense against phishing requires vigilance and multiple layers of security. Here are essential measures to reduce risk:
1. Identify Red Flags
- Watch for suspicious or misspelled URLs and domain names.
- Ensure websites use HTTPS with valid certificates before entering credentials.
- Be cautious of emails with urgent language, grammatical errors, or unknown senders.
- Verify unexpected requests through a separate communication channel.
2. Use Multi-Factor Authentication (MFA)
MFA adds an additional layer of authentication beyond passwords, such as SMS codes, authenticator apps, or security tokens. This greatly diminishes attackers’ ability to misuse stolen credentials.
3. Employee Awareness Training
Regular training programs and simulated phishing tests increase awareness and reduce the likelihood of successful employee-targeted attacks.
4. Adopt Advanced Email Security Solutions
Deploy email security gateways with AI and machine learning to detect suspicious links, attachments, and sender behavior before they reach users.
5. Leverage Zero-Trust Architecture
Zero-trust models assume no inherent trust for any user or device within or outside a network, enforcing strict identity verification and least-privilege access.
6. Monitor for Credential Exposures
Use dark web and breach monitoring services to identify if any organization’s credentials or data have been compromised, enabling fast incident response.
7. Utilize Tools to Detect Phishing on Websites
Website owners can check if their domains host phishing content using resources such as PhishTank or VirusTotal. Since many phishing pages reside on hacked websites, maintaining a strict website security posture is critical.
Conclusion: Staying Vigilant in a Phishing-Prone World
Phishing attacks are growing in complexity and frequency, posing a serious risk to individuals and organizations alike. Awareness of phishing tactics, combined with strong technical defenses like MFA, advanced email filtering, and ongoing training, form the cornerstone of effective protection.
By recognizing phishing indicators and adopting best practices, users can significantly reduce their chances of falling victim to these cyberattacks.
Stay informed, verify communications, and protect your data to combat phishing risks effectively.



